SNAT’s are commonly referred to as port forwards on other vendor platforms. See below how to create a typical RDP Port Forward from a known address.
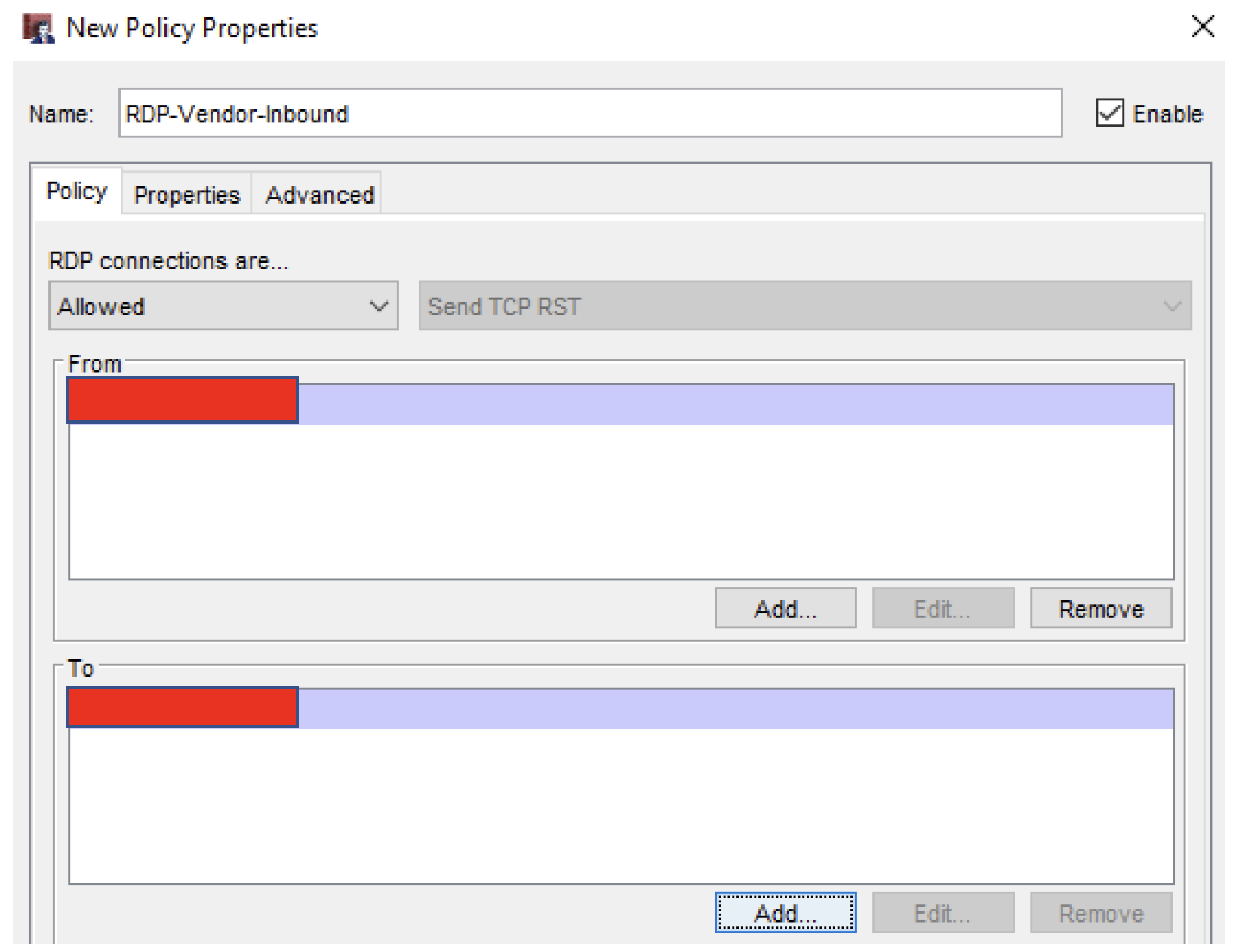
In Policy Manager, select Add Policy➔Packet Filters➔RDP
The policy window appears
Name the policy appropriately
Add the external IP that the RDP request will initiate from. Never open an RDP port forward from ‘Any-External’
In the ‘To’ Field, select Add➔Add SNAT➔Add
The following window will appear:
Name the SNAT Action appropriately, then select Add
At this point, a few items need to be addressed:
If the primary IP on the external interface is to be utilized, that IP can be selected with Set source IP unchecked
If the backup IP on your external is to be utilized, that IP must be added as a secondary, as follows:
Network➔Configuration➔Interfaces➔External Interface➔Secondary tab➔Add backup external IP referenced prior
Without completing this step, that backup IP address cannot be utilized, even though it may be a part of the block of static IP’s purchased from the ISP
Below the external interface/IP section, select the type of internal address: IP or FQDN. In this scenario, IP was utilized
Set internal port to a different port
If the RDP rule utilized in this example was not 3389, with this, the port could be forwarded to 3389. The inverse of this could be true if the server/device is configured to accept RDP on a non-standard port. Ensure that the connection incoming through the Firebox is lining up with what the end device is configured for. In the shown example, port forwarding was not necessary.
Below is the completed SNAT
Select OK➔OK➔OK➔OK
Review the completed policy, ensuring ports on the policy, and port forwards on the SNAT Action are correct
SNAT’s are a powerful tool in a NGFW’s arsenal. Just be cautious with how open these policies are made. Our recommendations would be to narrow the IP addresses down to as few as possible.