When you create an IPSec VPN on your Firebox, by default a policy is created that allows significant access to your network. Depending on how you configured the VPN initially, it could also grant the mobile VPN user unfiltered access to the Internet through the WatchGuard Mobile VPN connection. These two items combined leave your network susceptible to threats coming in through the mobile VPN user’s traffic and leave the potential for overutilization of your bandwidth.
In order to lock down the access that your Watchguard Mobile VPN users have, you can create additional policies to implement some of the firewall’s security features. To start, you first need to go to the Mobile VPN with IPSec tab in the WatchGuard Policy Manager.
Next, look for the policy that was automatically created when you set up your IPSec VPN. If you review this policy, you will see that it is allowing traffic to any internal and any external resource. Additionally, this policy is open on any port. If you leave this policy in place, access through the mobile VPN will be unfiltered.
To secure this mobile VPN traffic, we typically recommend that this default policy be edited or removed and replaced with policies that specify the access needed. This depends on how you want your mobile VPN used. There are numerous scenarios that can be used, but we have outline the three most common.
Method 1: Access To Internal Resources on All Ports, No Web Access
If you want your mobile VPN users to be able to get to internal resources on any port but not web resources, you can simply edit the default mobile VPN policy. All you will need to do is remove Any-External from the policy.
Please note that the 0.0.0.0\0 resource allows access to all devices on your network. If you want to specify a particular device or subnet, remove this entry and replace it with the host or network IP(s) that you desire.
Method 2: Access To Internal Resources on Specific Ports, No Web Access
If you want your mobile VPN users to be able to get to internal resources but want to restrict the ports available, you can remove the default policy and replace it with the ports you want. For example, if users only need RDP access when connected to the mobile VPN, you only need to create an RDP policy. To do this, while on the Mobile VPN with IPSec tab, add a new policy. Select the mobile VPN profile that this policy will be applied to.
Then, select the policy you want to create. In this example, we choose the RDP packet filter.
When this policy is created, it will default to referencing Any-External and 0.0.0.0\24. Make sure to remove Any-External. Then you can choose whether to allow RDP access to all internal devices by using the 0.0.0.0\24 resource, or by adding the host or network IPs that you want to allow.
Method 3: Access to Internal Resources, Web Access
If you want your mobile VPN users to be able to get to internal resources, you can start by editing the default policy as outlined in Method 1 to remove Any-External. Then, you will need to add policies to control web traffic. To do this, while on the Mobile VPN with IPSec tab, add a new policy. Select the mobile VPN profile that this policy will be applied to.
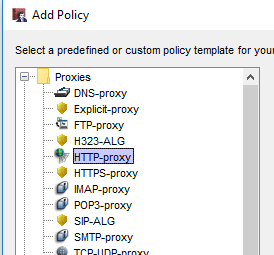
Then, select the policy you want to create. If you are trying to limit web traffic, you will need an HTTP proxy, an HTTPS proxy, and a DNS proxy.
Once the policy is added into your list, you can edit it just like a normal policy. You can apply a proxy action to this policy and use settings that you are already using on your internal web traffic.
With whichever method you choose, the final step is to finish applying your services. Make sure that your WatchGuard Subscription Services like Gateway Antivirus, IPS, RED, Application Control and WebBlocker are applied to these new policies. If you have APT Blocker or Data Loss Prevention, these will need to be implemented as well. Also, don’t forget to turn on logging on these new policies so that you can monitor the traffic!