The most efficient way to deploy custom certificates for Watchguard's Deep Packet Inspection (DPI) in a Windows environment is to set them to propagate through Active Directory Group Policy. Even if you have a mixed environment (Windows, Mac, Linux, Etc.) this is an easy way to handle the Windows based computers.
Remember, Windows computers inherently trust anything that is pushed form a Domain Controller. So by trusting the certificate on the Windows Domain Controller and setting it to deploy, your computers will trust the certificates.
Step 1: On the Domain Controller, navigate to the Certificate Portal of the firewall. This can be accessed by going to http://<IP of Interface>:4126/certportal
Step 2: Once you access the Certificate Portal, download the certificate that is available.
Step 3: Open Group Policy Management. Right-click on the Default Domain policy, and select Edit.
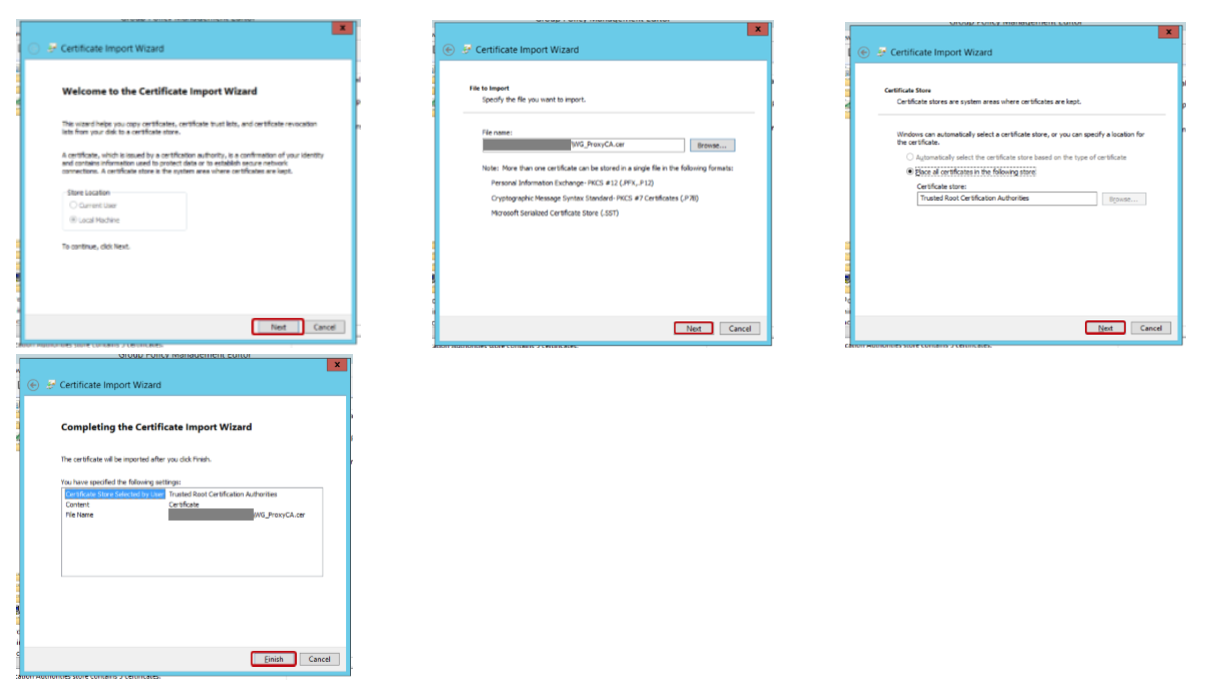
Step 4: Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies > Trusted Root Certificate Authorities. Select Action > Import
Step 5: Install the certificate.
Step 6: Make sure all devices that will be utilizing DPI are rebooted. This will cause the computer to grab the new trusted certificate from the server.
Step 7: Test by making sure HTTPS Content Inspection is turned on in the firewall and you can successfully access HTTPS pages. You can view instructions for that here.
Related Posts:
Configuring WatchGuard HTPPS (DPI) Inspection
Deploying a WatchGuard DPI Certificate on a Mac